"Global Privacy Controls": A new initiative to help people exercise their rights; Facebook's CFO says its personalized advertising business model has been attacked by changes to Apple's privacy policy;
"Global Privacy Control": a new initiative to help people exercise their rights;
Facebook CFO says personalized advertising business model under attack from Apple privacy policy changes
Five French bar and coffee shop managers arrested for not recording user logs on Wi-Fi;
China prepares to launch antitrust investigation against Google
A group of hackers found 55 Apple product-related vulnerabilities and received a reward of more than $50,000;
The U.S. Department of Defense announced $600 million for 5G military experiments;
The United States has seized 92 websites used by Iran to spread false information
Global Privacy Control: A new initiative to help people exercise their rights

Companies and individuals launched the Global Privacy Control (GPC) initiative on Wednesday to help users enforce their rights under the California Consumer Privacy Act (CCPA) and the General Data Protection Regulation (GDPR), foreign media Neowin reported. Proponents say the new rights make no sense if people are too hard to benefit from.
Support for "Global Privacy Control" includes Ashkan Soltani from Georgetown Law School, Sebastian Zimmeck of Wesrian University, The New York Times, The Washington Post, Financial Times, Automatic (WordPress.com and Tumblr), Glitch, DuckDuckGo, Brave, Mozilla, Disconnect, Abine, Digital Content Next (DCN), Consumer Reports, and the Electronic Frontier Foundation.
Supporters of the GPC say the CCPA gives Californians the legal right not to sell their data by letting browsers signal to businesses that they have opted out. Unfortunately, these signals do not have a clear or accepted technical standard, so users do not have an easy way to inform businesses of their preferences.
The organization has launched an experimental phase where people can download browsers and extensions from Abeine, Brave, Disconnect, DuckDuckGo and EFF to tell participating publishers that they don't want their data to be shared. Looking ahead, the people behind the GPC want to develop an open standard that many organizations can eventually support;
Supporters of the GPC say they look forward to working with California's attorney general to make the GPC legally binding under the CCPA. They also want to make GPC applicable to other global laws, such as the GDPR.
Facebook's CFO says its personalized advertising business model has been attacked by changes to Apple's privacy policy
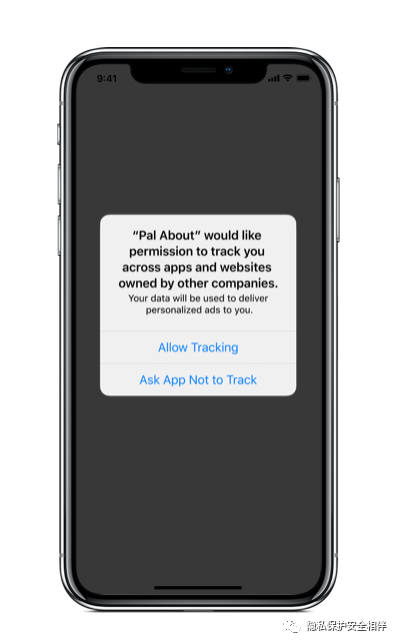
Facebook's chief revenue officer said Tuesday that its business model, which relies on personalized advertising, is being "attacked" by iOS 14 privacy changes. These changes include a new feature that requires users to opt-in to tracking on a per-app basis through The Trace for Advertiser, or IDFA tags. Although originally planned for a generic version of iOS 14, Apple delayed the launch of the feature until 2021 after public protests from companies including Facebook, which earns most of its revenue from advertising services.
"The tools that entrepreneurs and businesses now rely on are under threat," David Fischer, Facebook's chief financial officer, said in a digital speech on Advertising Week on Tuesday. For me, apple's proposed changes are quite radical and hurt developers and businesses the most. He singled out the changes to IDFA in iOS systems.
The Facebook executive also said the company plans to "defend" its business model, which it sees as valuable in tracking users, in contrast to Apple's thinking. Fisher calls Apple's business "a business that sells luxury hardware or subscription services, primarily for consumers like us who are fortunate enough to have a lot of discretionary income in some of the world's richest countries." "
While Apple has positioned the changes as a privacy-supporting measure, Facebook isn't the only company worried about them. Media companies and publishers are "preparing" for changes to IDFA, and in September a group representing the advertising industry urged a "dialogue" on the proposed feature.
Five French bar and coffee shop managers have been arrested for not recording user logs on wireless networks

At least five bar and coffee shop managers have been arrested in the French city of Grenoble for not keeping user logs on the free WiFi network provided in the store. They are accused of violating a 14-year-old law that requires all Internet service providers to keep user logs for at least a year. Bar and coffee shop owners say they are unaware of the law and believe it does not apply to them. But local media say the law applies not only to ISPs in a broad sense, such as telecommunications service providers, but also to anyone who provides Internet services such as wiFi networks without or without passwords. The managers of the bars and coffee shops were released after being questioned. By law, they face up to a year in prison, up to a maximum of 75,000 euros and a maximum commercial fine of 375,000 euros.
China is preparing to launch an antitrust investigation into Google

Google pulled out of the Chinese market a decade ago, but some of its products are still popular in China, most notably the Android operating system. China is preparing to launch an antitrust investigation into Google over allegations that it used Android's dominant position to obstruct competition, Reuters reported, citing people familiar with the matter. The charges were brought by Huawei, and China's antitrust regulator has submitted them to the State Council for review. People familiar with the matter said a decision on whether to launch a formal investigation could be made as soon as October, with a decision likely to be influenced by China-U.S. relations. Another person familiar with the matter said it would also investigate allegations that Google's market position could cause "extreme damage" to Chinese companies such as China, such as China, because losing the US tech giant's support for the Android operating system would result in a loss of confidence and revenue.
A group of hackers found 55 Apple product-related vulnerabilities and received a reward of more than $50,000
A group of hackers has been awarded more than $50,000 for discovering 55 vulnerabilities in Apple's system. Sam Curry, Brett Buerhaus, Ben Sadeghipour, Samuel Erb and Tanner Barnes spent three months hacking Apple's platforms and services and discovering a range of weaknesses. The 55 vulnerabilities identified by the team vary in severity, some of which are so severe that they describe them as:
In the course of our engagement, various vulnerabilities were discovered in the core part of Apple's infrastructure that would allow an attacker to completely hack into customer and employee applications, even launch a worm that automatically takes over the victim's iCloud account, retrieve the source code for Apple's internal projects, completely hack into the industrial-controlled warehouse software used by Apple, and take over conversations with Apple employees, and gain access to management tools and sensitive resources.
Apple quickly addressed most of the vulnerabilities after receiving the report, some of which were resolved in just a few hours.
Overall, Apple responded very quickly to our report. For our more important reports, the time from submission to repair is only four hours.
Some of the team's work could be well paid as part of Apple's security bounty program. As of Sunday, October 4, they had received four payments totalling $51,500. These include $5,000 to disclose the full name of iCloud users, $6,000 to discover IDOR vulnerabilities, $6,500 to enter the enterprise's internal environment, and $34,000 to discover system memory leaks that contain customer data.
Since no one really understood their bug bounty program, we were almost entering uncharted territory and investing so much time. Apple's history of working with security researchers is interesting, but their vulnerability disclosure program appears to be a big step in the right direction to work with hackers to secure assets and get interested people to discover and report vulnerabilities.
Apple has been actively investing in its bug bounty program since last year. Security researchers can now earn up to $1 million per vulnerability, depending on the nature and severity of the vulnerability.
With permission from Apple's security team, the team released a wide-ranging report detailing a range of vulnerabilities and ways to locate and exploit them. They also hinted that more rewards might be on the way.
The U.S. Department of Defense announced $600 million for 5G military experiments

The U.S. Department of Defense announced it would provide $600 million for 5G experiments at five military bases, foreign media CNET reported. The tests will focus on virtual reality training, robotics and drones, and the Defense Department said Thursday that 5G is "critical to national and economic security."
The test sites are at the Naval Base in San Diego, Hill Air Force Base in Utah, Joint Base Lewis-McJorde in Washington State, Marine Corps Logistics Base in Albany, Georgia, and Nellis Air Force Base in Las Vegas. The experiment will include:
San Diego Naval Base: Intelligent storage and material transportation between naval forces and onshore facilities, connecting with AT&T, and using autonomous drones, biometrics and robots.
Lewis-McJorde Joint Base: Mixed reality training, connectivity with AT&T and Samsung, and prototype combat training programs using AR and VR.
Albany Marine Corps Logistics Base: Smart warehouse for storing and maintaining vehicles.
Nellis Air Force Base: Develop 5G technology for "air, space and cyberspace lethality" and work with AT&T to achieve 5G connectivity.
Hill Air Force Base: Enable Air Force radar to share spectrum with 5G cellular services, develop antenna systems with Nokia, and develop machine learning with Ericsson.
The United States has seized 92 websites used by Iran to spread false information

The U.S. Department of Justice has seized 92 websites that are said to have been used by Iran's Islamic Revolutionary Guard Corps to spread false information. Four of the domain names - Newsstand7.com, usjournal.net, usjournal.us and twtoday.net - are disguised as real news organizations based in the United States, which the Justice Department has determined are controlled by the Iranian Guards. According to documents released Wednesday, the sites appear to target Americans for Iranian propaganda about U.S. domestic and foreign policy.
According to the Justice Department's statement, the other 88 domain names are aimed at audiences in Europe, the Middle East and Southeast Asia, while also claiming to be genuine local news sites that actually operate to spread pro-Iranian false information. Google, Facebook inc. and Twitter Inc. helped the FBI investigate. Threat researchers at FireEye Inc.'s Mandiant division also discovered the seized domain names in 2018. At the time, according to Mandiant, the Iranian Guard's business was peddling anti-Saudi, anti-Israel and pro-Palestinian themes, while also promoting specific U.S. policies deemed favorable to Iran, including the U.S.-Iran nuclear deal.
All of these seized domain names are owned and operated by U.S. companies. The seizure was carried out under the International Emergency Economic Powers Act, which gives the President of the United States broad powers to regulate financial transactions in a state of emergency. In 1979, President Carter used the same tool to freeze Iran's financial assets in the United States during the hostage crisis.
The Justice Department says the IRGC's use of these domain names violates the Foreign Agents Registration Act, which requires foreign agents in the United States to publicly declare their identities so that the U.S. government and its residents can understand the sources of information and the identities of those who "attempt to influence U.S. public opinion, policies, and laws." It added that these domain names for Americans were never registered under FARA.

Go to "Discovery" - "Take a look" browse "Friends are watching"